This is a re-run of an article I wrote for Security Current which was based on a presentation I delivered at the IQPC Cybersecurity in Higher Education Conference in March of this year.
As the flagship campus in the UW System and a major research institution in a state with open record statutes that respect privacy while insisting on accountability, it is important not to tip the delicate balance between securing private information and living in the open society of an R1 university.
In living the Wisconsin Idea – the notion that what we learn and discover should be applied to solve problems and improve health, quality of life, the environment, and agriculture for all citizens of the state…and beyond – we occasionally create the need to really know where the important data is stored and a deep understanding of how that data is supposed to be managed.
It’s all about the data!
Data rich environments like UW-Madison present an interesting laboratory for answering tough legal and ethical questions about data privacy and security. The CISO needs to know where the legal and ethical landmines are placed in the fields of security and privacy. How much security is really required in an environment where openly shared data and research results fuel business?
With the regulatory environment that surrounds most of the information needed to manage students, staff and faculty, security of that information is a risk management driver. That same data can also provide value to many campus researchers to advance our understanding of education, social interactions, human ecology, medical diagnosis and treatment, infectious diseases, and anything to do with bratwurst and cheese.
Guided by federal and state law and the ethical standards of our profession, the challenge is this; how should higher education approach data privacy from a policy and process perspective? CISOs need to know which vector to focus on when dealing with privacy issues; people, process or tools.
Security Is Easy! Privacy Is a Challenge…
Privacy is a simple term for two complicated concepts; information privacy and autonomy privacy. At its most basic layer, privacy is people exercising control of their personal information and attributes.
Information privacy laws protect individuals by requiring security controls be placed around information about the individual in order to prevent unauthorized disclosure. HIPAA, FERPA and State Data Breach Notification laws are full of examples that define what is required for protection of personal information.
Business rules that prevent staff contact information from being published on websites are a practical example of using privacy controls. Corporations that choose to shield their staff from open access to the public promote the cause at minimal expense – and arguably greater benefit as their staff are able to focus on their daily tasks instead of fielding calls from vendors and telemarketers
You see – security is easy!!!
Autonomy privacy protects individuals by shielding them from unwanted surveillance which includes behavioral monitoring or profiling. This aspect of privacy is at the foundation of important concepts like academic freedom and freedom of speech.
The National Strategy for Trusted Identities in Cyberspace published a set of Fair Information Practice Principles which were designed to promote enhanced privacy in the conduct of online transactions. Affectionately called FIPPs, these principles are a widely accepted framework for defining guidelines to be used in the evaluation and consideration of systems, processes, or programs that affect individual privacy. Of the principles shown in graphic below, in this CISO’s opinion the most important are:
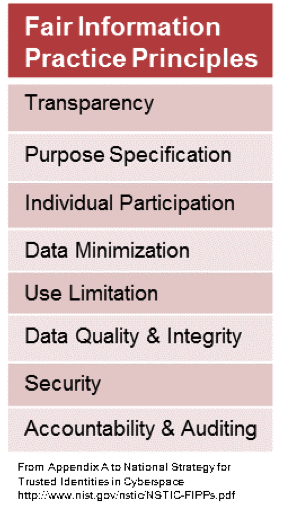
- Transparency
- Organizations should be transparent and notify individuals regarding collection, use, dissemination, and maintenance of personally identifiable information (PII).
- Individual Participation
- Involving the individual in the process of using PII and, to the extent practicable, seek individual consent for the collection, use, dissemination, and maintenance of PII.
- Purpose Specification
- Articulating the authority that permits the collection of PII and the purpose or purposes for which the PII is intended to be used.
- Data Minimization
- Collecting only the PII that is directly relevant and necessary to accomplish the specified purpose(s) and only retain PII for as long as is necessary to fulfill the specified purpose(s).
Application of the full set places organizations in the right position to promote confidence and trust – in this case with online transactions – and also to form better relationships with owners and curators of personal data stores internal to an organization.
Of course there are also data security and privacy concerns with social media – where students and staff willingly give away personal information. Have any of the lawyers in the room ever tried to use a Facebook profile to prove authorization to release information?
Security is easy – establishing rules that promote privacy is hard!
The CISO’s Role
Where privacy and security matters are concerned, the CISO is more than just another corporate cost cutter, technologist or policy developer. To guard the corporate image, or in my case a university’s reputation, the CISO must accept the role of evangelist.
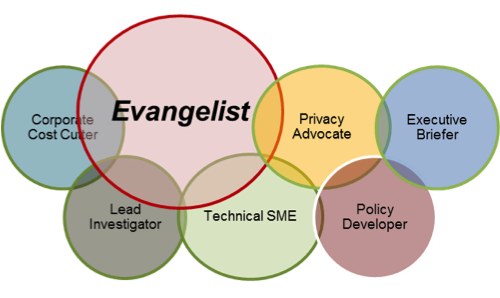 Preaching the righteous gospel of security and privacy fuels the average user’s ability to feel safe in the digital world created for their convenience. Just as a customer at a shopping mall should expect a certain level of safety from the landlord and retailers, an online privacy environment at your university should have the same trust factor.
Preaching the righteous gospel of security and privacy fuels the average user’s ability to feel safe in the digital world created for their convenience. Just as a customer at a shopping mall should expect a certain level of safety from the landlord and retailers, an online privacy environment at your university should have the same trust factor.
The CISO must be prepared to increase the number of regular prayer meetings used to preach the righteous gospel of awareness in data security and privacy practices.
Ethics is a choice – and is useful for (or against) success
Here is the dilemma. We know that with each technology or procedural control, equal and opposite reactions are possible. Encryption can protect data or it can be used to shield research results as they are extracted through insider activity. It doesn’t take an ethical wizard to see the problems if we do not protect data in transit or at rest – so where do you focus the technology and training around data protection?
To sum it all up…
It is not a small point that we live in interesting times and have much to do to ensure we are not only good network citizens, but that we do all within our capabilities to keep the personal data in the right place with the right protections without impeding our ability to share data as necessary. In higher education, we do this to advance research and enable the highest quality of teaching and learning
As CISOs, we all strive to pursue a deeper understanding of the threats to data in a relentless search for mitigating controls and vulnerability remediation. From an ethical perspective, we should always be on watch to ensure we are good stewards of our data, information systems, and resources.
The higher education CISOs need to live our own university version of the Wisconsin Idea and taking from what we learn about the intersection of security and privacy, return value to our constituents – and beyond.
As always, I appreciate your feedback. Simple rules – be nice, be fair and be honest.
Please email your thoughts to cybersecurity@cio.wisc.edu and we will periodically post them with helpful answers.
Next Blog: How secure are your HR records and student data?
