The CISO’s Perspective / Special Edition
Over the last several weeks the UW–Madison Cybersecurity Operations Center has observed two significant events along with several minor to important episodes which should cause all of us to pause and ask ourselves the following question: What should I be doing to keep my data and our information systems and networks safe?
If you are like many people, this question usually follows a major announcement or a series of news stories about cybersecurity. In all seriousness, these events are largely FUD – a cyber-geek term meaning fear, uncertainty and doubt. FUD is not a useful state of being as it causes people to do irrational things like disconnecting from useful technology sources and moving to a reclusive home network with fewer safeguards than our UW–Madison network, hoarding data like bottled water and D-cell batteries prior to a big snow storm, and desperately searching for their, most likely non-existent, data backup and recovery plans.
Two recent events I think are instructive are a Google Docs phishing scam that broke the last few days in April and the ongoing WannaCry ransomware attack that started late in the week of May 8th.
Google Docs phishing scam
Staff at organizations representing multiple industry verticals, including over 500 users at UW–Madison, reported receiving emails which look nearly identical to the actual ones Google Drive sends when someone shares a document. Many of the emails include the address in “hhhhhhhhhhhhhhhh@mailinator.com” in the “send to” section.
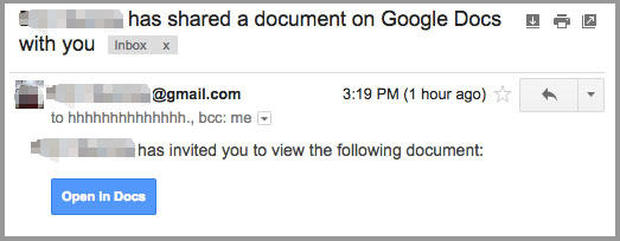
This email about a Google Doc appears to be from someone the user knows, but is actually a phishing attempt.
If you were to click on the “Open in Docs” link, you would be taken to a fake Google page where you would be asked to grant “Google Docs” access to all of your Google accounts. This would expose your email and private documents. In addition, the malicious code would access your Google Contacts list and send a similar email to everyone on that list.
This is particularly concerning at UW–Madison since many who use Google Docs also use Gmail and we know that some folks forward University Office 365 email to their personal Gmail account.
The lesson: Know your data. Know where it lives and what the rules are for that server or service. Know your data’s friends. And finally, know who wants to share data with you and when they want to share it.
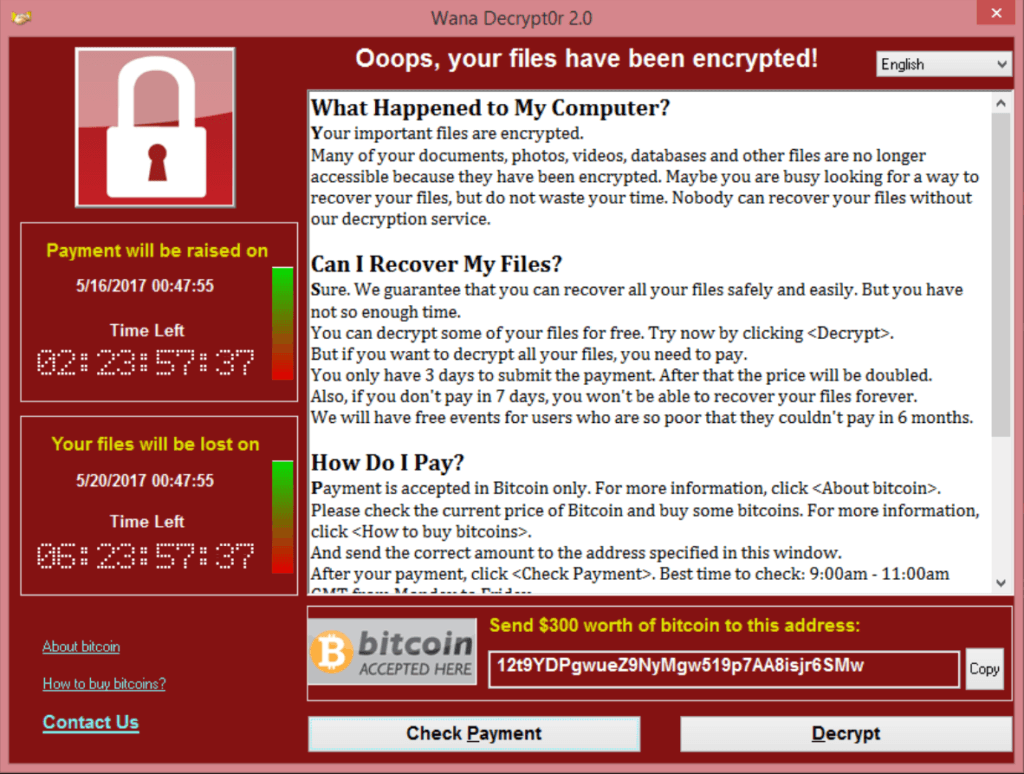
WannaCry ransomware outbreak
It started out in the IT systems of around 40 national health systems at hospitals and healthcare organizations across the UK. The strain is called “Wanna Decrypt0r” which asks victim machines to pay a $300 ransom to decrypt their computers. The malicious attack campaign is called WCry and is also referenced online under various names, such as WannaCry, WannaCrypt0r, WannaCrypt, or Wana Decrypt0r. Fear has driven non-emergency medical procedures to be suspended and ambulances are being diverted as a result of the attack.
The hack of a National Security Agency exploit database has been listed as an enabler to the cyber criminals that started these events in motion.
Non-health focused organizations around the world are also being affected, including Spanish telecommunications firm Telefonica, which reported a serious issue affecting its internal network as a result of this outbreak. In one bit of good news, a researcher learned how to stop the malicious code temporarily by flipping a switch within the code string. No doubt the next event will have that code deployed without that safeguard.
The lesson: Back up your data. You can easily rebuild your system but can you rebuild years of hard work embodied in your research data?
At UW–Madison, the Office of Cybersecurity’s Incident Response and Forensics team have temporary safeguards in place for both of these threats and are sharing them with Divisional Information Security and IT Service teams. We are working closely with the Mail Team and other DoIT service providers to ensure the right counter-measures are found, developed, refined and made available.
But we can’t catch everything. Malicious actors are already working on that next exploit!
As always, I appreciate your feedback. Simple rules – be nice, be fair and be honest.
Please e-mail your thoughts to cybersecurity@cio.wisc.edu and we will periodically post them with helpful answers.