Imagine you are a business leader at a large organization and were just told that your most valuable information was extracted from your information system and replaced with random ones and zeros. How about if you were on a large research project and your last five years’ worth of data was replaced by a very well-done cat video? Or perhaps, you were editing that term paper in your learning management system knowing your professor wants it delivered by midnight, but the paper is now missing in action.
How did that happen?
Data loss can happen – large or small, unstructured or formatted, simple files or complex databases – they could all go away from “natural causes” or hacker activity. Perhaps your data is lost because of an inside job. Internal threats occur when, for example, a malicious internal user abuses their permissions and attempts to move data outside the organization.
Data can be lost through unintentional or negligent data exposure. Many data leaks occur by employees exposing sensitive data on public websites or social media.
Many cyber-attackers target sensitive data where they penetrate the security perimeter using techniques like spear phishing, malware or code injection. Their objective is to gain access to valuable or marketable data like personal healthcare information or credit card data.
What is Data Loss Prevention?
Data loss prevention (DLP) is the name for a popular cybersecurity and business strategy for making sure that sensitive or critical information does not “leak” outside the corporate network. The term is also used to describe software products that help network administrators automatically or manually manage what data end users can transfer within the network or to other sources. For example, if you want to transfer large data files to a server outside your network, your administrator might require encryption be set before the data transfers, or that the data can only go to a specific server. They might also require that you use an “air gap” method for files exceeding a specific value to save network resources.
DLP software products use a variety of business rules to classify and protect critical or classified information so that unauthorized end users cannot accidentally or maliciously share data, which if disclosed could place your organization at risk. DLP tools could prevent an employee from forwarding a business email containing patient data outside the corporate domain or warn you and system administrators if you tried to upload a corporate file to a cloud storage or sharing service like Drop Box, GitHub, or your personal Google account.
DLP – Strategy, Tactics, and Tools
As a CISO, I strongly believe in the AIC Triad – which stands for the three fundamental aspects of cybersecurity; Availability, Integrity, and Confidentiality. The characteristic of availability is, in my CISO opinion, the most critical of the three. As you think of the AIC triad in relation to DLP, you will agree that loss of data availability is essential to defend against.
Adoption of DLP is being driven by threats of external hackers, insider threats from untrained or disgruntled employees, and with increasing importance, the more rigorous foreign government, Federal or state privacy laws – many of which have stringent data access and protection requirements. Imagine if your data were “owned” by someone else who formally asked you to ensure their data would be returned upon completion of your research project. On the “day of reckoning” when you discovered that data was removed from the system and inadvertently destroyed by a well-meaning, but somewhat clumsy apprentice; my hope is that you implemented a data backup strategy six months before you had read this blog and asked your IT support team to get a DLP solution in place; and that they were successful in fielding that solution. When they showed you how to operate it last month you decided that in addition to the warning and countermeasures in the tool they installed, your tactics would be to perform a weekly backup of that data to your off site storage service using tools offered by DoIT or your local IT support team, and that on this past Friday you had checked to see if the DLP solution was working.
UW-Madison is working on that first step right now. The Office of Cybersecurity is looking at candidate tools and will be working closely with the Madison Information Security Team (MIST) to set up a DLP service within the next few months.
It’s more than a backup strategy…
In addition to being able to monitor and control endpoint activities, some DLP tools can be used to filter data streams on the corporate network and protect data in motion.
DLP solutions prevent data loss from multiple of sources. Use DLP to enable or enhance your business continuity program and allow recovery of data and systems that meet your time to recover and recovery point objectives. If you have backup data stored where you can get it to meet critical business or personal needs, DLP can prevent data loss across our enterprise!!!
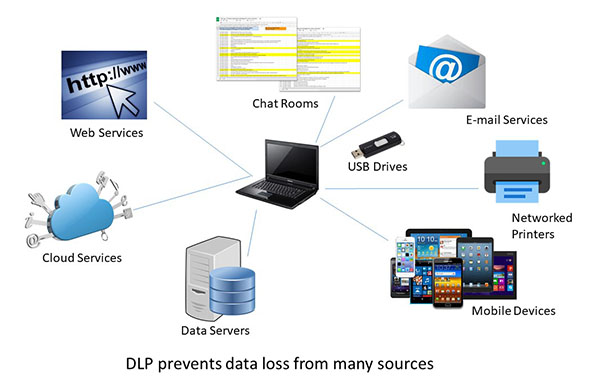
Many of the current generation of DLP products may also be referred to as data leak prevention, information loss prevention or extrusion prevention products. DLP can enhance the goals of data visibility. Using a DLP can assist in your needs to comply with regulations to protect UW-Madison Restricted Data such as Personally Identifiable Information (PII). DLP can ensure that you protect intellectual property critical to your research project and profitable to the university.
DLP solutions can also be integrated with other tools like Mobile Device Managers that secure our mobile workforce and enforce security in Bring Your Own Device (BYOD) environments. And finally, DLP tools can be included in cloud deployments and contracts that require the university to secure data within on-premise cloud or remote-cloud services and systems.
Now for the next step
Come and meet Julie Johnson, the Data Loss Prevention Administrator on the Governance, Risk and Compliance team in the Office of Cybersecurity and join in the conversation at the October MIST meeting on Thursday, October 3rd from 2:00 to 3:30 pm in Room 3139 in the Computer Sciences and Statistics building.
Stay tuned as the Office of Cybersecurity continues to work toward the objective of providing Data Loss Prevention services.
Now, where is your data?
As always, I appreciate your feedback. Simple rules – be nice, be fair and be honest.
Click here to be directed to a Qualtrics Survey where you can give us your thoughts.
Next Blog: TBD
