This marks my first public blog post about the University of Wisconsin – Madison’s approach to securing our IT infrastructure to promote the availability of systems and data, ensure the integrity of computing operations and infrastructure, ensure personal or private information is held with the appropriate levels of confidentiality, and ensure required transactions that occur are provided with a sense authenticity which promotes confidence in both sender and receiver.
My favorite question is “what is keeping the CISO up at night. My internal response is there are too many good books to read and I have a weakness for television police dramas.
Okay – so the better answer is illustrated in this drawing I found on LinkedIn
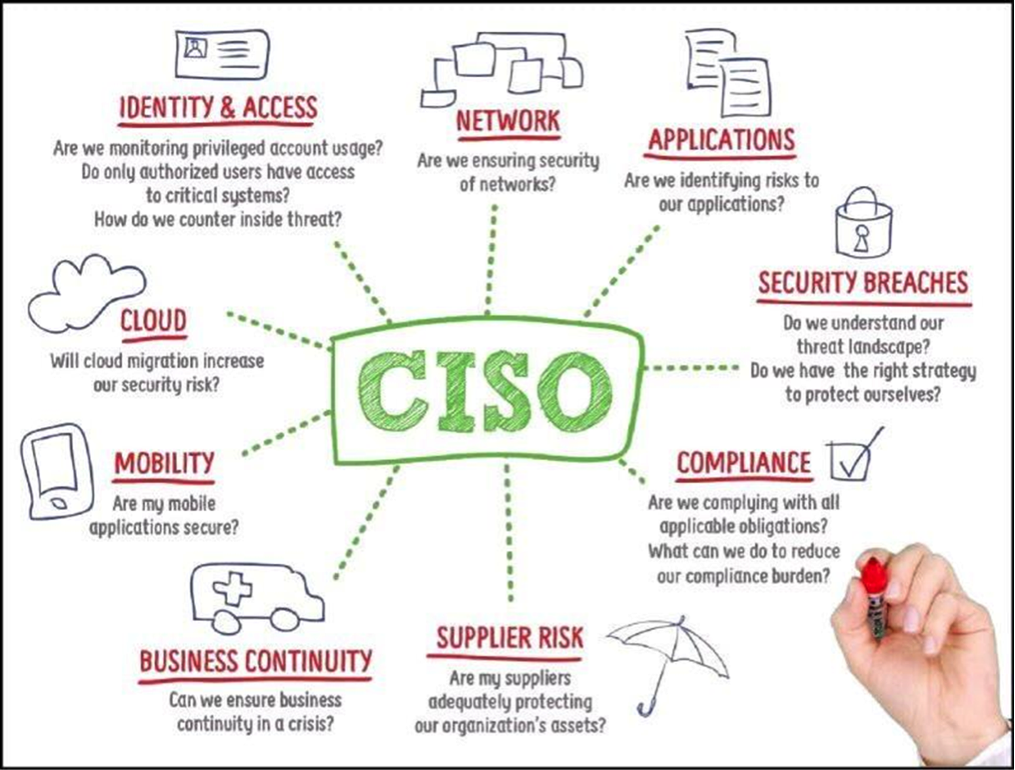
Of the areas above, I can narrow down my top five major worries at UW-Madison as:
- Security Breaches
This area includes having a good understanding of our networks and systems so we can accurately assess if and how the threats and threat actors will reveal themselves. We need a good strategy for each data type and where that data is headed while in motion, at work, and at rest. - Incident Management and Business Continuity
Or, more importantly, how we respond to cybersecurity events or incidents. If data is lost or systems are taken off-line, I worry about how soon we can return the data and system to full functionality. I also need to know if our cyber threat intelligence gathering and analysis is sufficient to guide our actions and those of our campus partners. - Compliance – The Risk Management Framework
This is one of the most important aspects of effective cybersecurity. What we know about our systems from a documentation and operational test and evaluation perspective. Check out my next blog entry to find out more! - Cloud
We are entering a new era in computing – and yes I know cloud services have been around for quite a while – but our pace of embracing the cloud is increasing and the new cybersecurity challenges are becoming more clear. How we scope and contract for the service is important if we plan to use the cloud for restricted or sensitive data management. - Mobility
The challenges of developing applications that meet security requirements for sensitive or restricted data must be met head on. It can be done and those who are our largest mobile community – our students – demand our best effort with the least overhead.
Enough about what worries me! Let’s talk about what makes me happy…
One of the not so best kept secrets at UW-Madison is how I feel about the team that makes up the Office of Cybersecurity and our principle supporters in the Office of the Chief Information Officer and Vice Provost for Information Technology; and the exceptional leadership and staff of the Division of Information Technology. I am also very happy with the Madison Information Security Team – known as MIST. These people are top professionals and extremely talented people who dedicate their life and careers toward building the best networks and securing your information systems from intrusion by one of the three classes of cyber adversaries: - Accidental insiders who allow social engineers to compromise their information and develop ways to exploit the good guy’s identity and perform bad acts for the notion of unearned personal or professional gain.
- Common Criminals that want to steal our information and monetize the product.
- Members of criminal syndicates or nation state sponsored cyber adversaries who look for ways to disrupt service, deface websites, or otherwise harvest our best ideas for wide scale crime or launch vindictive assaults on the university.
Okay, now that you have had a look inside my head, how about taking a moment to give me your feedback. Simple rules – be nice, be fair and be honest.
And, if you have not had a chance to review the UW-Madison Cybersecurity Strategy, I recommend you take a look at this link:Cybersecurity Strategic Plan
Next Blog: Managing Cybersecurity Risk
