As part of the next phase of the Smart Access program, the program team is sharpening our focus on how we mature the university’s Zero Trust capabilities. Cyber threats continue to grow more sophisticated and persistent, and our current safeguards are no longer enough. We need to continue to make progress towards meaningful risk reduction and maturing our adoption of Zero Trust in order to protect the university’s critical systems, data, and services from evolving threats.
Our approach is guided by two key frameworks:
- Protect surfaces help us prioritize what matters most—sensitive data, critical applications, and essential systems—so we can apply safeguards where they have the greatest impact.
- The Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model, based on NIST standards, provides a roadmap for how to improve capabilities across five core pillars and foundational elements including identity, devices, networks, applications, data, and visibility & analytics.
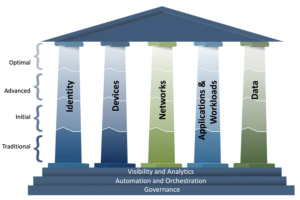
Together, these frameworks help us focus and measure our progress: the protect surface approach defines what we protect, and the CISA model helps us define how we improve.
Focus areas for the next phase
Our current work is centered around exploring three strategic focus areas:
- Continuing governance and collaboration to guide program direction and priorities, grounded in our principle: We’re all in this together.
- Advancing capabilities in Visibility & Analytics and Automation & Orchestration, to improve insight, responsiveness, and resilience.
- Improving maturity in the Devices pillar, with an emphasis on strengthening device compliance and integration.
We’re using the CISA maturity model’s “optimal” state as our long-term target. To move toward that goal, our work will include:
- Identifying what data and integrations are needed to support optimal Zero Trust outcomes.
- Assessing current-state capabilities, gaps, and opportunities.
- Prioritizing integrations based on impact and effort—focusing first on areas where we can make measurable progress quickly.
We’ll work collaboratively across DoIT and with IT partners and stakeholders throughout this phase. Be sure to sign up for our email list to stay informed about opportunities to contribute and help shape the future of the program.
A measurable, collaborative journey
Zero Trust maturity is a long-term effort. We’ll continue working across the university to identify protect surfaces, align our maturity goals, and implement controls that meaningfully reduce risk.
Our Smart Access program service principle Growth Through Measurable Impact will guide where we focus first. By combining clear priorities, collaborative planning, and maturity-based evaluation, we’re building a stronger, more resilient cybersecurity foundation for the university.
