This CISO’s Perspective blog is adapted from an article published in CIO Review online.
Here at UW-Madison, we are constantly reminded of the increasing threat to information, systems and data. Every day there is a new angle that threat actors, criminals and cyber punks (circle one) are taking to disrupt, destroy, or damage our ability to conduct research, teaching and outreach to our community and the State of Wisconsin. Higher education develops large and enticing volumes of research information, and within UW-Madison we hold tens of thousands of records with personal and financial information, and nearly two centuries worth of historical records. Likewise, the speed and complexity of current and pending technologies accelerates the pace of change and intricacy in the need to mature our cybersecurity posture and information protections.
Cybersecurity is a cultural issue that is more than just the latest tool or concept for finding and preventing evil within our corporate information and technology enterprise.
What are the measures of success for our cybersecurity program?
Many will tell you that avoiding the dreaded appearance on the six o’clock news is the primary measure of success in cybersecurity. A more reasonable approach is using metrics developed from our security framework. Many corporations choose a framework from sources like the International Standards Organization, the National Institute for Standards and Technology, or the Center for Internet Security’s 20 Critical Controls. Success is found in choosing the one that fits your organization’s technical information architecture, business models, internal dynamics, and external communications structure.
CAUTION! Frameworks are a baseline! Simply accepting the baseline is not always secure. Understand the value proposition…then supplement with controls that create the security your users deserve.
Success is knowing where your benchmarks are and establishing key performance indicators you can clearly see and easily measure.
Here at UW-Madison we chose from the National Institute for Standards and Technology (NIST) frameworks for risk management and cybersecurity operations.
How mature is your cybersecurity program?
If you are learning from your experiences, good or bad, you are maturing. Mature cybersecurity programs address operational practices with standards and compliance in mind. Success also depends on understanding C-level and board of directors-level concerns with organizational and investment priorities that match the prevailing risk appetite. The NIST Cybersecurity Framework includes a maturity model with tiers for policy, procedures, implementation, testing, and integration. This is useful in determining where the organization is within the cybersecurity core event life cycle of identify, protect, detect, respond and recover. Understanding where your program sits on the maturity path will help you to determine success.
Success in the early stages of maturity is still success!
UW-Madison’s program was evaluated by a third party earlier this year. Our program was evaluated against the NIST model as “risk and threat aware” for identifying threats and recovery from events. We were assessed as having “repeatable” processes for protect, detect and respond characteristics.
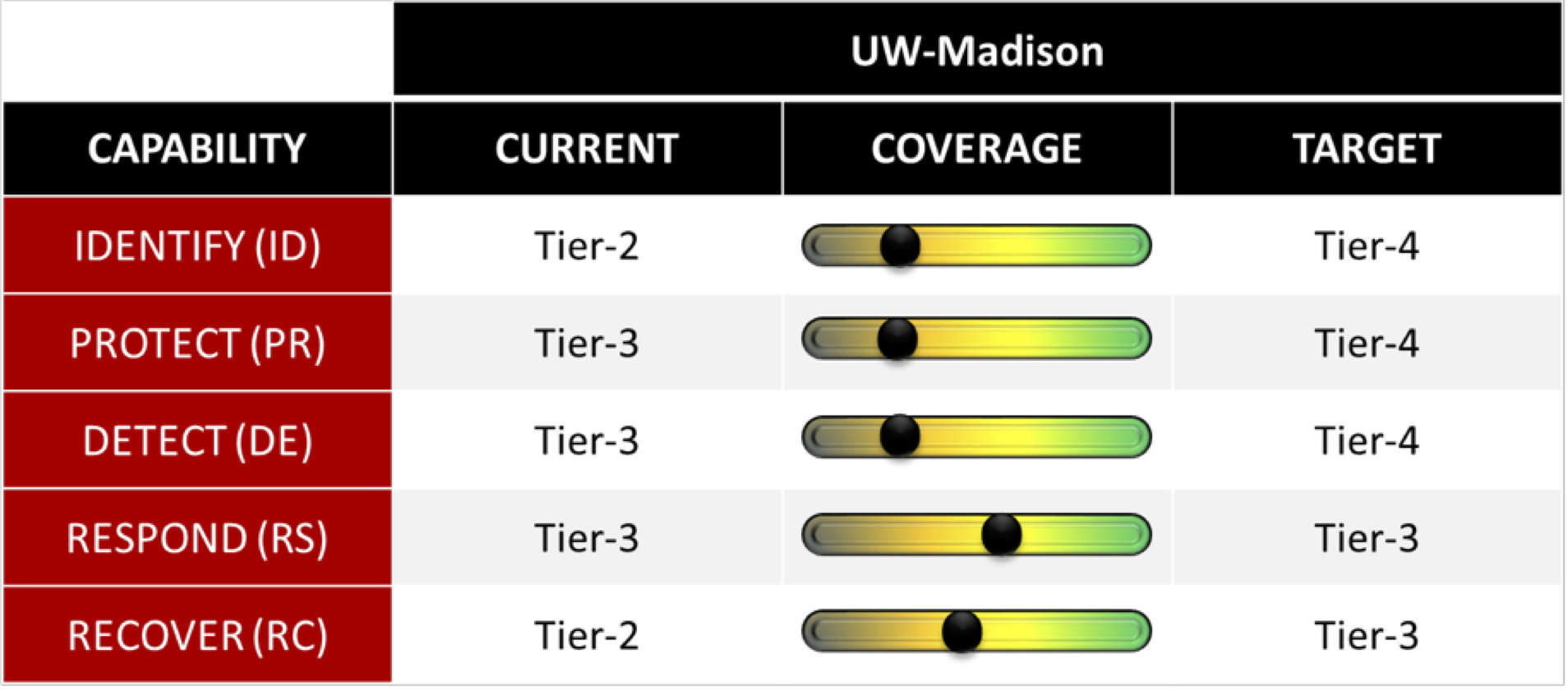
Thanks to recent investments in people, processes and technology, the Office of Cybersecurity will be working with the UW-Madison community to implement new tools and services that will drive us toward Tier-4 in all five areas within the next 18 months.
What are your cybersecurity strategy and guiding principles?
Once you have a handle on the way your program will work and an understanding of the program’s maturity, the energy should shift to developing and implementing a strategy containing policy, standards, and implementation plans. At UW-Madison, we started with a strong and relevant set of Guiding Principles – know your data, know your architecture, and know the industry-related issues (FERPA, HIPAA, GLBA, etc.) We are working hard to understand our environment to include assets and attributes like hardware, software, and standard configurations.
We are also aware of the revolution in privacy concerns – as the landscape changes and new systems are developed, my advice is to bake in the right security controls now! UW-Madison understands and incorporates the emerging privacy principles, law and doctrines such as the European Union General Data Protection Regulations or the California Consumer Privacy Act of 2018. We are continually learning how to address employee behaviors and workplace issues, and then incorporate business and organizational best practices.
Success is having the community agree to these guiding principles. You cannot socialize enough on this task.
How often do you “talk cyber” to your constituents and stakeholders?
Communications and awareness are key to moving the program from paper, charts and graphs to real culture change. We are getting better at understanding UW-Madison’s tolerance for negative messages and seek to avoid those that invoke fear, uncertainty and doubt (my preference – avoid FUD as much as possible – but then I am a glass-half-full guy). We also have the ability to sort through the vendor hype for real information worth sharing.
Through our exceptional CIO Office communications group led by Brian Rust and Mary Evansen, and with partnerships developed through the Madison Information Security Team (MIST) and the MIST communications subteam, we continually adjust our focus to communicate early and often using messages the university community understands. Not that we are always perfect in developing the messages people want to hear, it’s that we seek to develop our message(s) with a cross section of academic, research, business, IT and security groups in mind. Above all, we have a written communications plan that encourages constant and consistent messages, including ways to address leaders and executives, manage crisis communications, and communicate change.
We encourage and use the feedback received and are careful not to make large changes from small amounts of imperfect data. We involve our community through education and feedback focused on key performance indicators. Cybersecurity is like Novocain, you sometimes need to give it a bit of time to work before you start poking around with sharp instruments.
Success occurs when we express our message in organizational terms and examine feedback to track trends, then report.
A successful program…
…is not a bolt-on for projects to check a requirements block. Successful cybersecurity programs incorporate frameworks and best practices that change the organizational DNA. To meet our missions for teaching, research and outreach, the UW-Madison cybersecurity program has to be an integral part of the culture and mature in providing the right people, processes and technology – at the right cost – at the right time. We are striving to make YOUR cybersecurity program a value center instead of a cost center.
“Successful cybersecurity programs are core to the business and never exceed the value of the information and systems the program is designed to protect.”
Next time we’ll talk specifics about the cybersecurity investment and the initiatives we will be bringing to UW-Madison.
As always, I appreciate your feedback. Simple rules – be nice, be fair and be honest.
Please e-mail your thoughts to cybersecurity@cio.wisc.edu and we will periodically post them with helpful answers.
Next Blog: TBD
